Information Security
Probing Texts
Last modified 2/13/2025
WOW! I'm suddenly so popular!
Analyzing Scam Text Messages: Social Engineering Tactics in Action
The text messages shown in these images exhibit characteristics commonly associated with scam attempts, particularly those that rely on social engineering tactics. These messages aim to establish contact, build trust, and ultimately manipulate the recipient into engaging with the scammer. While they appear harmless or casual, their vague and generic nature suggests an attempt to deceive recipients into responding.
Characteristics of These Scam Messages
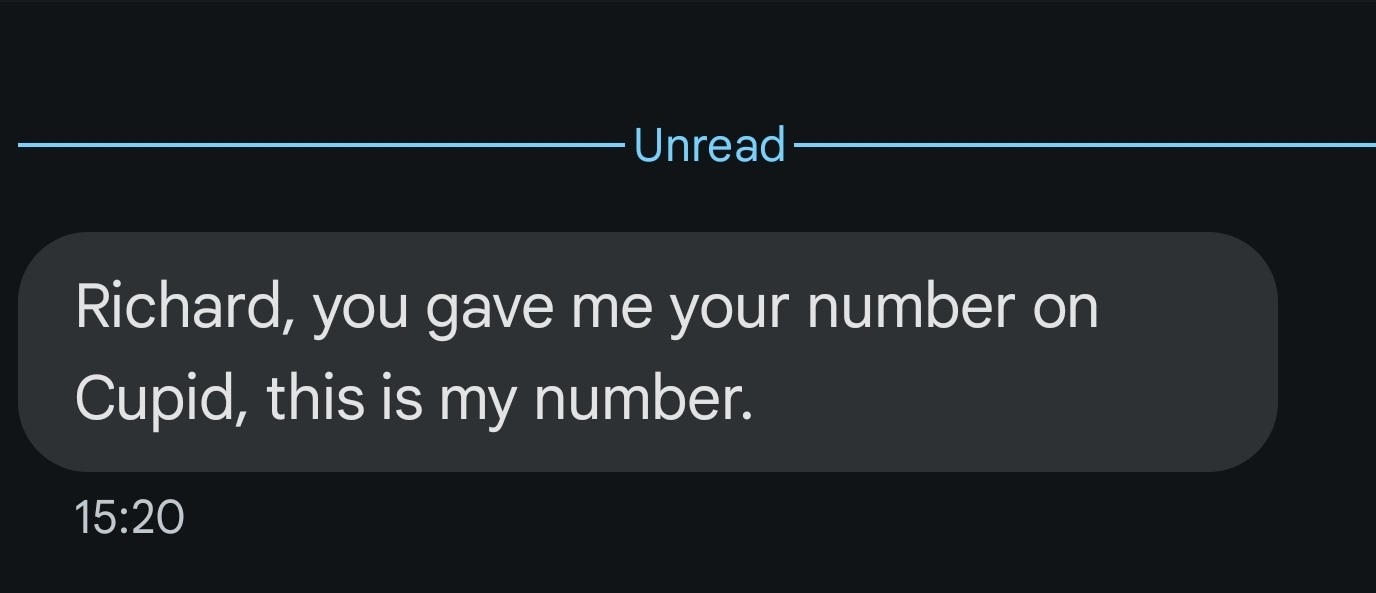
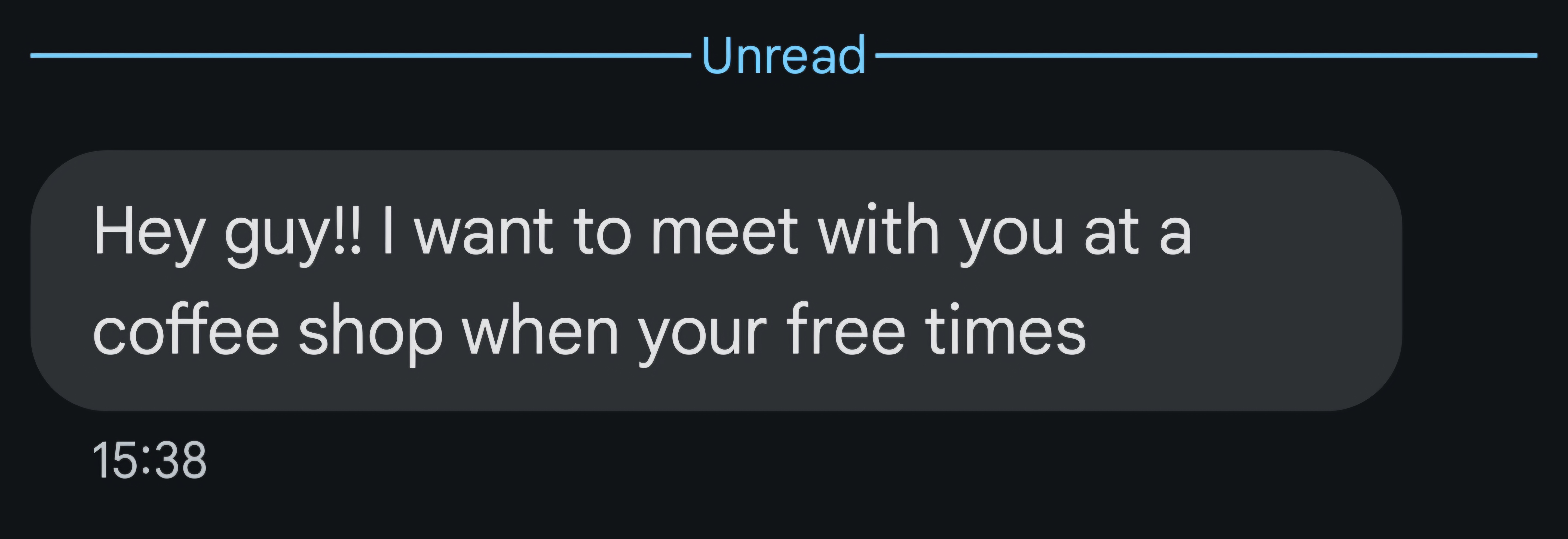
Use of Common Names and Generic Greetings
- The messages use common names to appear personal, yet they are not necessarily directed at the correct recipient.
- Some messages, such as "Hey guy!!" and "Hi," are intentionally vague so they can be sent to multiple people without customization.
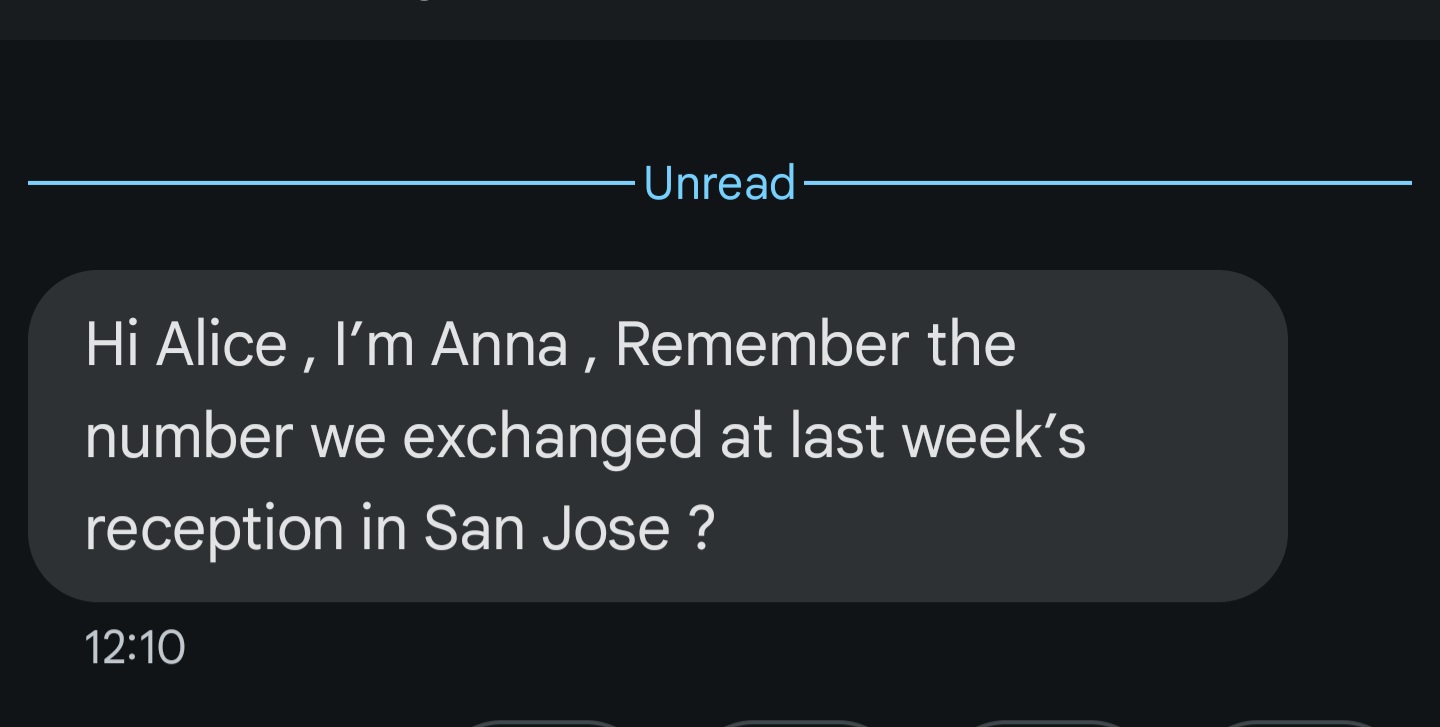
Attempts to Build Immediate Familiarity
- The messages reference past events that may or may not have happened
- By implying that the recipient has already interacted with the sender, scammers encourage engagement without suspicion.
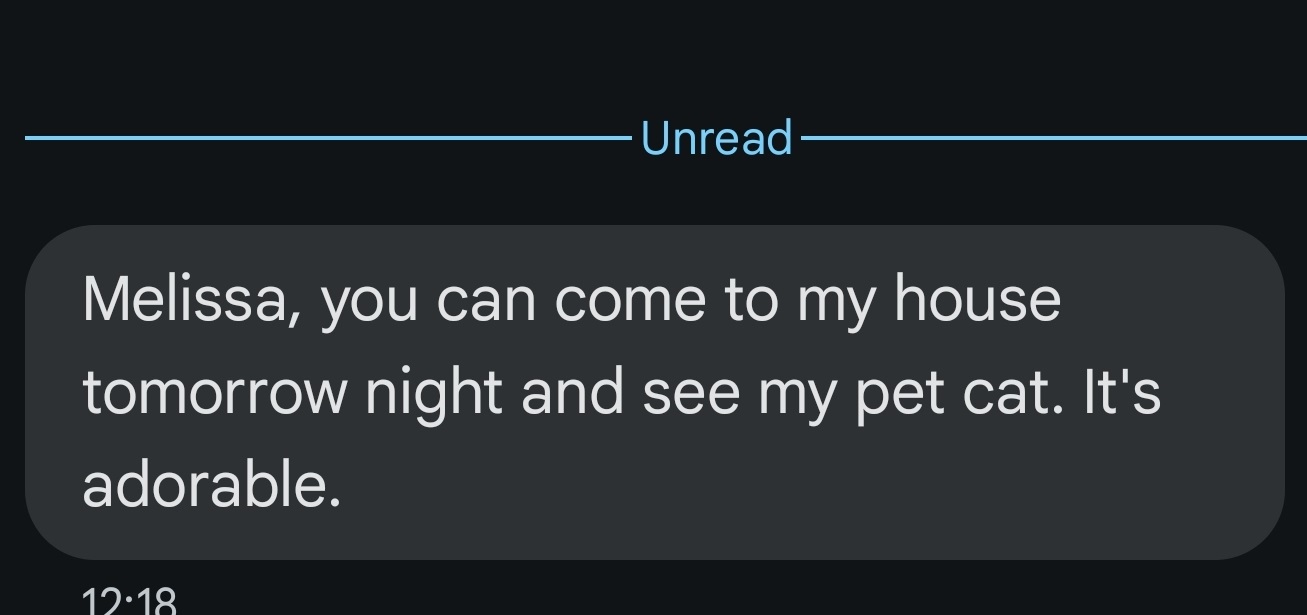
Casual Invitations to Meet
- The message is just a way to drive interaction
- These invitations are an attempt to get the recipient to confirm their availability and possibly share personal details.
Vague and Poorly Written Texts
- Scammers often send messages with grammatical errors, awkward phrasing, or incorrect spelling
- This suggests that the messages may have been automated or sent by non-native speakers attempting to cast a wide net.
Why Scammers Use These Tactics
Scammers use these types of messages for several reasons:
To Elicit a Response
- A simple "Who is this?" or "I think you have the wrong number" is enough to confirm that the phone number is active and belongs to a real person.
- Once a scammer receives a response, they can escalate the interaction to phishing attempts, romance scams, or fraudulent schemes.
- Malicious actors can also use your response to craft a better message for the next time they contact you.
To Exploit Curiosity or Confusion
- Messages like "long time no see" or "Remember the number we exchanged?" create a sense of curiosity, making the recipient wonder if they might actually know the sender.
- This psychological trick can lead someone to engage further instead of ignoring or blocking the message.
To Establish Trust Before Requesting Personal Information
- By pretending to be someone familiar or friendly, scammers build a false sense of trust, making it easier to extract sensitive information later.
- This technique is often used in romance scams, where fraudsters gradually gain the victim’s confidence before making financial or personal requests.
To Lead to a Bigger Scam
- If the recipient responds, the scammer may try to shift the conversation toward a fraudulent scheme, such as:
- A phishing attempt (asking for sensitive information like bank details or passwords).
- A financial scam (requesting money for emergencies or fake investments).
- A malware attack (sending malicious links or attachments).
How to Deal With These Messages
- Do Not Reply: Even responding to say "wrong number" can confirm your phone number is active.
- Block the Sender: If the message feels suspicious, block the number immediately.
- Report the Message: Many mobile carriers allow users to report scam texts by forwarding them to designated numbers.
- Avoid Clicking Links or Sharing Information: Never share personal details, even if the message seems familiar.
Conclusion
Don't Click, Don't Respond. Block and Delete!